Threat-Detection
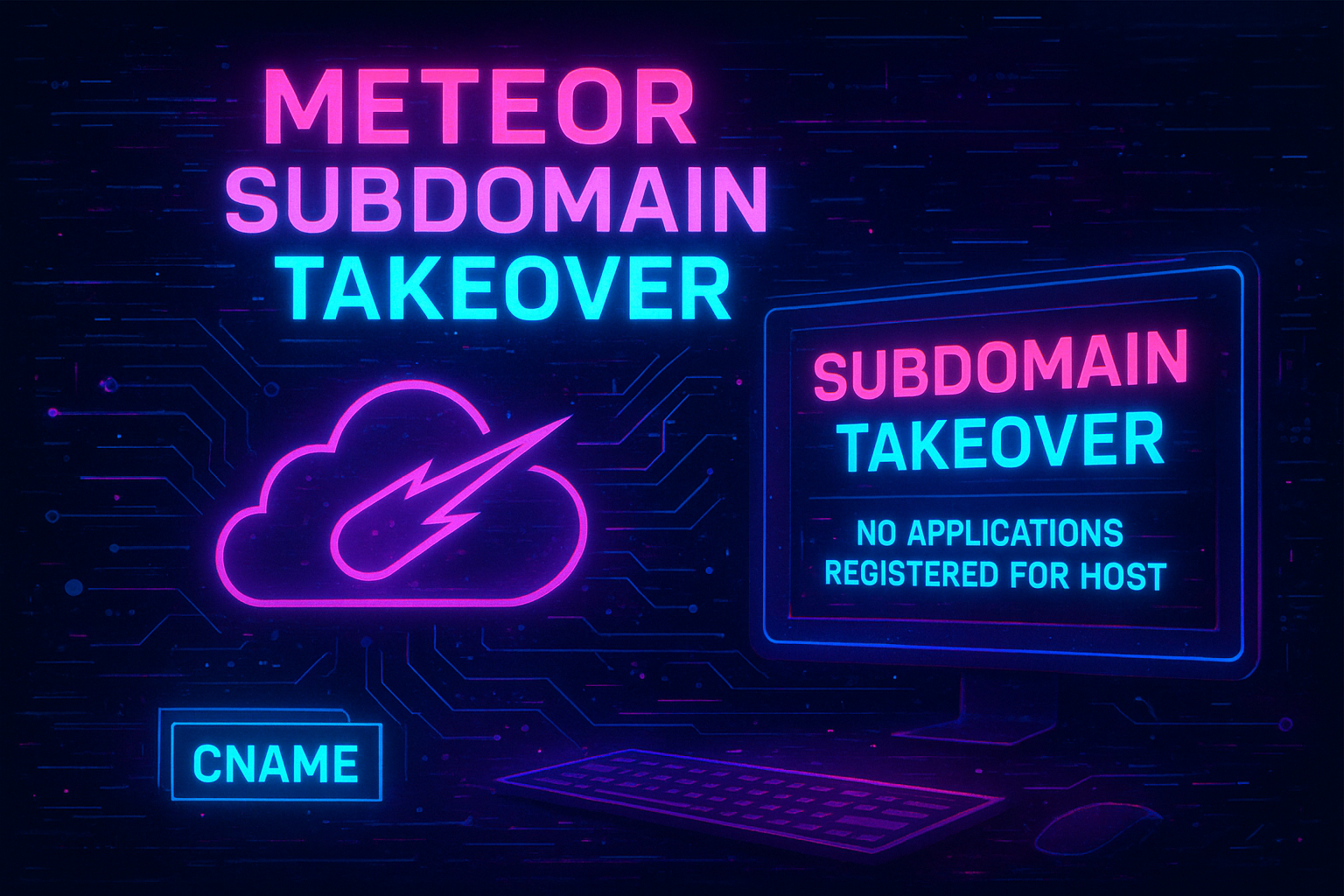
Meteor Subdomain Takeover: Attack Techniques and Prevention Strategies
Understanding Subdomain Takeover
Subdomain takeover occurs when an attacker gains control over a subdomain of a target domain by claiming an unclaimed or …

Data Breach Search Exploitation: How Attackers Weaponize Leaked Credentials
How Attackers Search Through Data Breaches
Data breach exploitation has evolved from opportunistic attacks to sophisticated intelligence operations that pose …
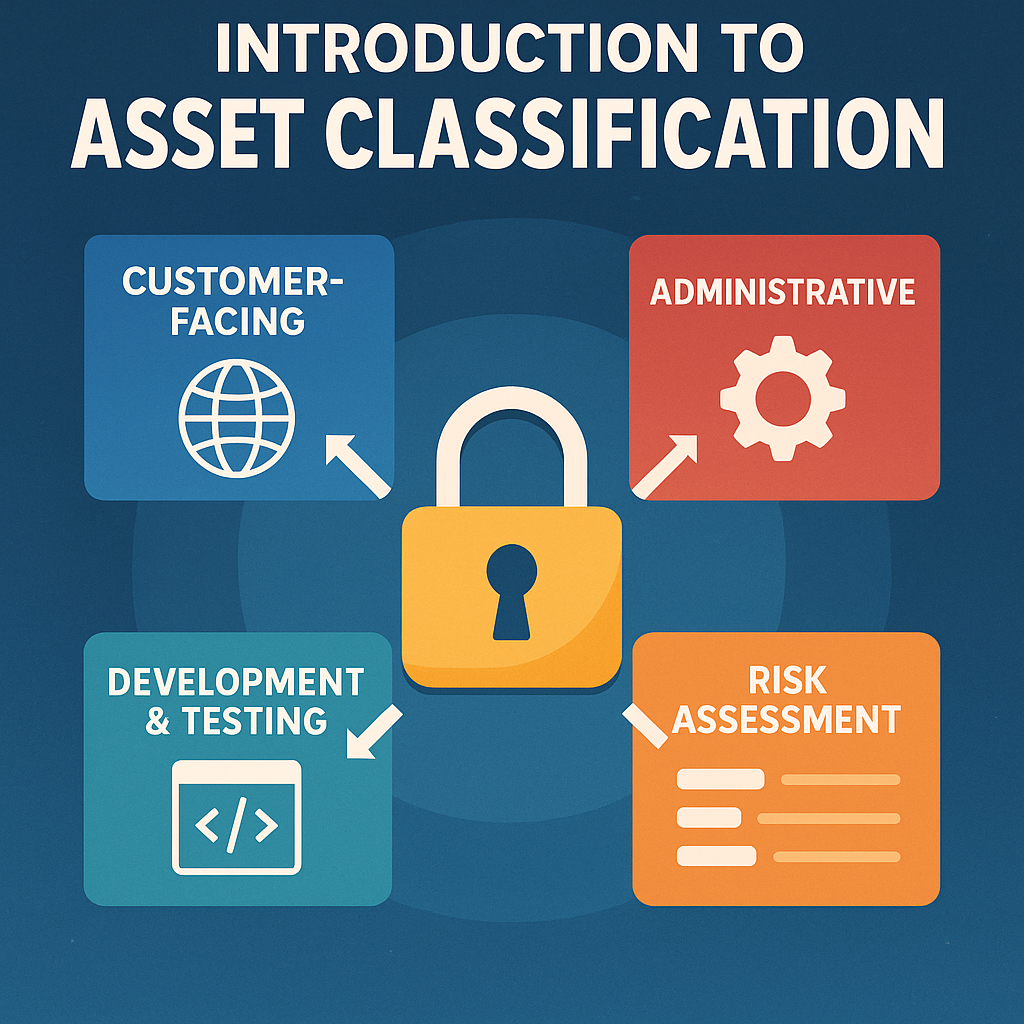
Attack Surface Management: Asset Classification and Risk Assessment
Introduction to Asset Classification
Once you’ve discovered your external attack surface, the next critical step is classification and risk assessment. …

Attack Surface Management: Asset Discovery Methodologies and Techniques
Introduction to Asset Discovery
Asset discovery forms the foundation of any effective Attack Surface Management program. The goal is to identify all …

Attack Surface Management: Continuous Monitoring and Change Detection
Introduction to Continuous Monitoring
Attack Surface Management is not a one-time assessment but an ongoing process of monitoring your organization’s …
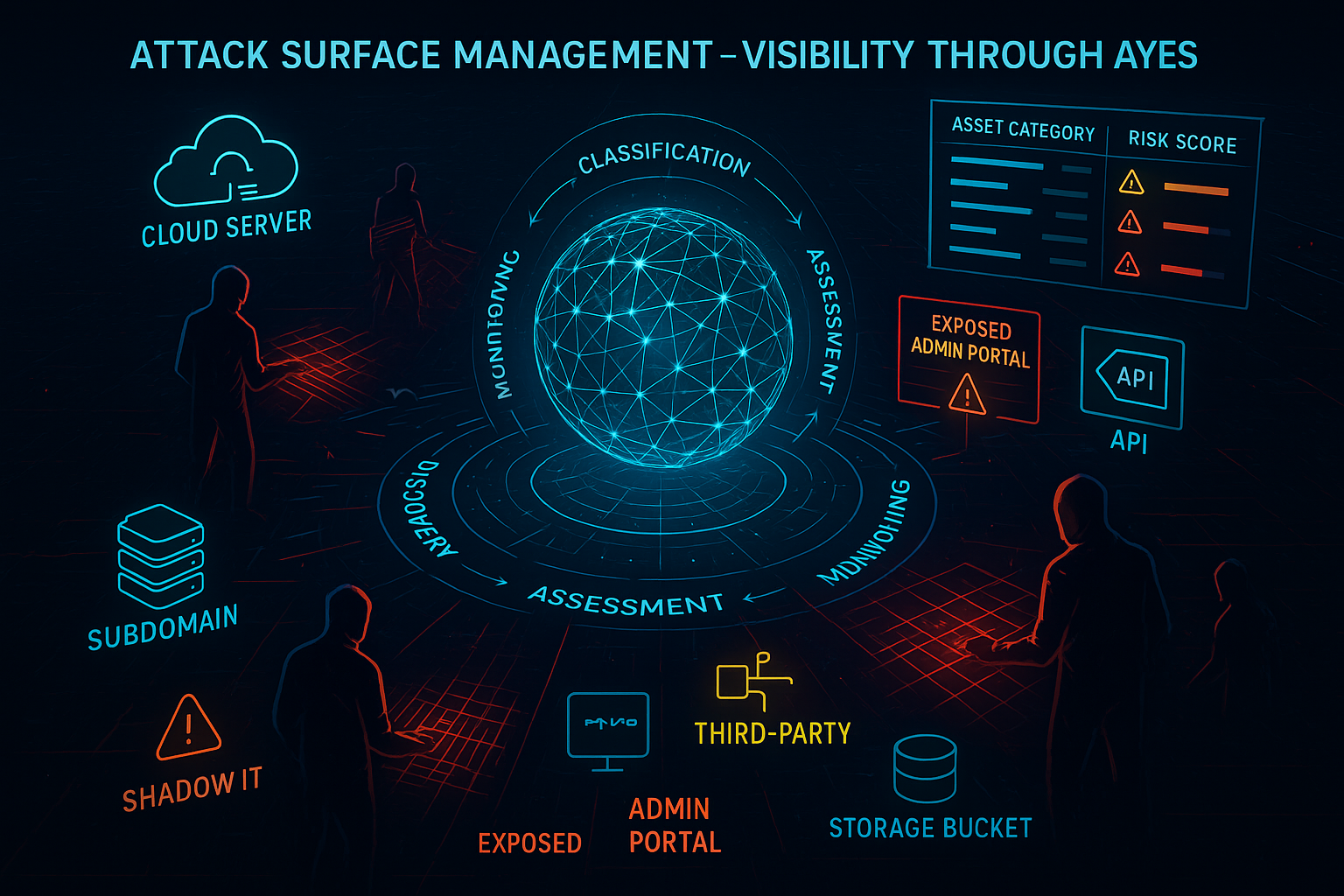
Attack Surface Management: Fundamentals and Core Concepts
What is Attack Surface Management?
Attack Surface Management (ASM) is the continuous process of discovering, cataloging, and monitoring all internet-facing …

DNS Security in Cloud Environments: Advanced Defense Strategies Against Modern Threats
Introduction: The Critical Role of DNS Security in Modern Cloud Infrastructure
The Domain Name System (DNS) serves as the foundational layer of internet …