Network-Security
Advanced network security techniques, protocols, and defensive strategies. Learn about network monitoring, intrusion detection, firewall configurations, and secure network architecture.

Data Breach Search Exploitation: How Attackers Weaponize Leaked Credentials
How Attackers Search Through Data Breaches
Data breach exploitation has evolved from opportunistic attacks to sophisticated intelligence operations that pose …

Attack Surface Management: Asset Discovery Methodologies and Techniques
Introduction to Asset Discovery
Asset discovery forms the foundation of any effective Attack Surface Management program. The goal is to identify all …

Attack Surface Management: Continuous Monitoring and Change Detection
Introduction to Continuous Monitoring
Attack Surface Management is not a one-time assessment but an ongoing process of monitoring your organization’s …
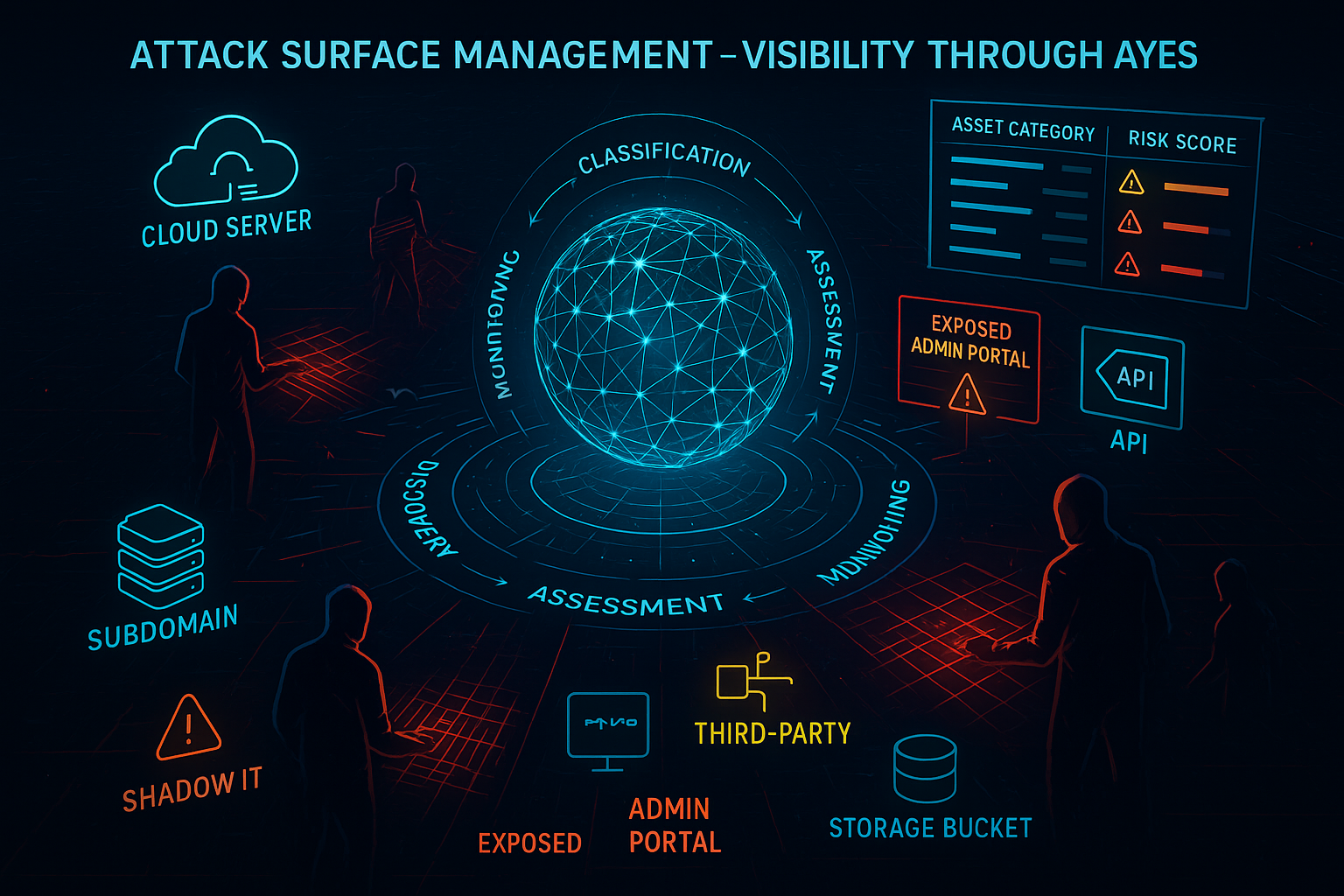
Attack Surface Management: Fundamentals and Core Concepts
What is Attack Surface Management?
Attack Surface Management (ASM) is the continuous process of discovering, cataloging, and monitoring all internet-facing …

DNS Security in Cloud Environments: Advanced Defense Strategies Against Modern Threats
Introduction: The Critical Role of DNS Security in Modern Cloud Infrastructure
The Domain Name System (DNS) serves as the foundational layer of internet …