Attack Surface Management: Fundamentals and Core Concepts
Attack Surface Management Fundamentals: Complete Guide to ASM Basics
What is Attack Surface Management?
Attack Surface Management (ASM) is the continuous process of discovering, cataloging, and monitoring all internet-facing assets that could serve as entry points for cyber attacks. According to the NIST Cybersecurity Framework 2.0, organizations must maintain comprehensive visibility of their attack surfaces to implement effective cybersecurity controls. Unlike traditional asset management, ASM operates from an external perspective - seeing your organization exactly as attackers do.
The fundamental principle of ASM is simple: you cannot protect what you cannot see. Modern organizations have digital assets scattered across cloud providers, business units, and third-party services, many of which exist outside traditional IT oversight.
Series Overview:
- Part 1: ASM Fundamentals ← You are here
- Part 2: Asset Discovery Methodologies - Comprehensive discovery techniques
- Part 3: Asset Classification & Risk Assessment - Risk-based prioritization
- Part 4: Continuous Monitoring & Change Detection - Real-time monitoring and alerts
The Evolution of Attack Surfaces
According to the Verizon 2025 Data Breach Investigations Report, 68% of breaches involved assets that organizations were unaware they possessed.
Traditional IT Era (1990s-2000s)
- Centralized infrastructure
- Clear network perimeters
- Limited external-facing services
- Manual asset inventory feasible
Cloud Era (2010s-Present)
- Distributed infrastructure
- Dissolving network boundaries
- Rapid service deployment
- Automated discovery essential
Modern Challenge Organizations now typically have 2-5x more internet-facing assets than they can manually track. A medium-sized company might have:
- 200+ domains and subdomains
- 50+ cloud services
- 100+ third-party integrations
- 500+ API endpoints
ASM vs. Traditional Asset Management
Traditional Asset Management focuses on known, owned assets within organizational boundaries. It relies on:
- IT procurement records
- Configuration management databases (CMDB)
- Network scanning of known ranges
- Manual documentation processes
Attack Surface Management assumes incomplete knowledge and operates from an external perspective:
- Discovers unknown and forgotten assets
- Monitors third-party and partner connections
- Tracks ephemeral cloud infrastructure
- Uses attacker reconnaissance techniques
Core Components of Attack Surface Management
The MITRE ATT&CK Framework documents how adversaries use reconnaissance techniques during initial attack phases, making comprehensive ASM essential for defense.
1. Asset Discovery
External DNS Infrastructure Your DNS footprint extends far beyond your main domain. Subdomains often reveal:
- Development and staging environments
- Administrative interfaces
- Legacy applications
- Third-party integrations
Example Discovery Pattern:
company.com
├── www.company.com
├── api.company.com
├── admin.company.com (potentially exposed)
├── dev.company.com (should be internal)
├── staging.company.com (unintended exposure)
└── legacy.company.com (forgotten system)
IP Address Ranges Organizations own or lease IP space that may host:
- Web applications
- Mail servers
- VPN endpoints
- Legacy systems
Cloud Infrastructure Modern cloud deployments create dynamic assets as documented in NIST SP 800-210:
- Container registries
- Serverless functions
- Storage buckets
- API gateways
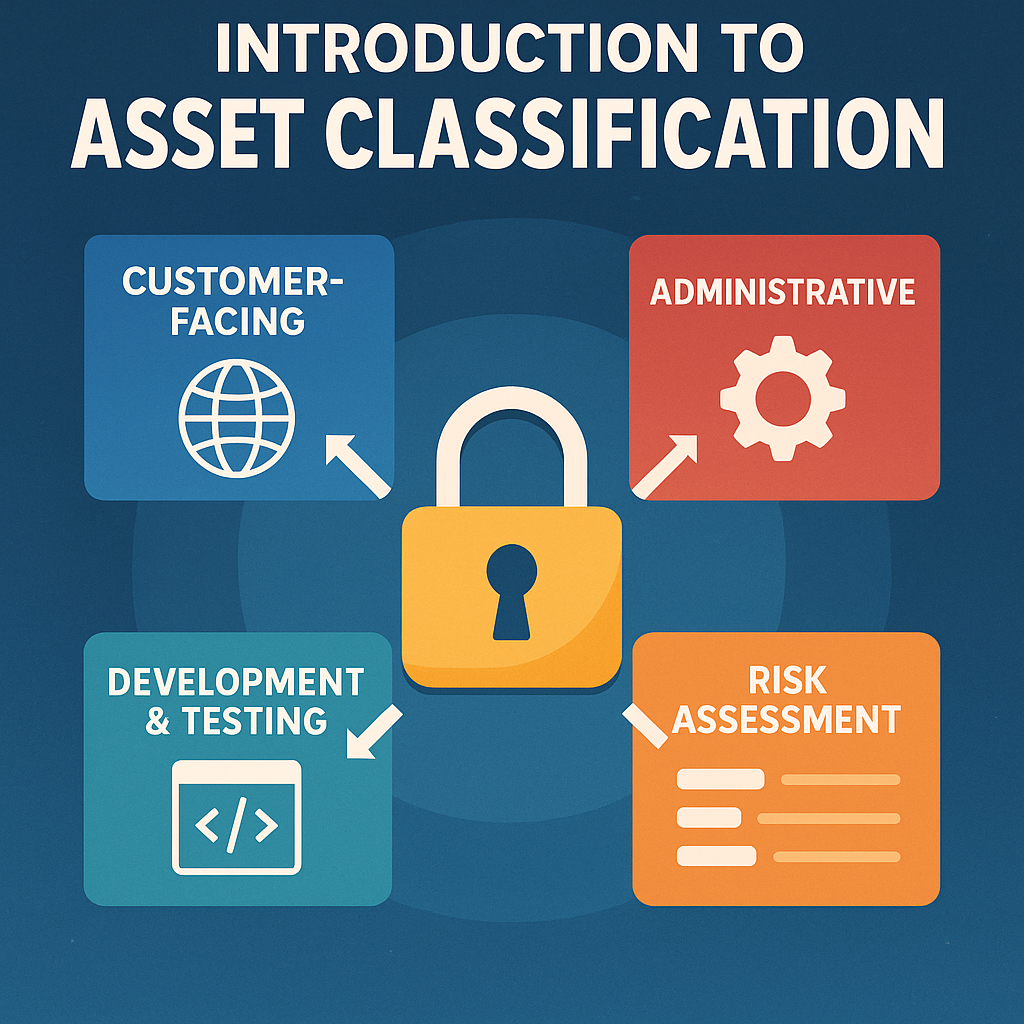
2. Asset Classification
By Business Function
- Customer-facing: Public websites, portals, APIs
- Administrative: Management interfaces, control panels
- Development: Testing, staging, CI/CD systems
- Integration: Partner APIs, third-party connections
By Risk Level
- Critical: Customer data, payment systems, administrative access
- High: Business applications, internal tools
- Medium: Marketing sites, documentation
- Low: Archived content, redirects
By Ownership
- Owned: Direct organizational control
- Managed: Third-party services you configure
- Monitored: Partner systems affecting your security
3. Continuous Monitoring
Change Detection
- New subdomain creation
- Service deployment
- Configuration modifications
- Certificate updates
Threat Intelligence Integration
- IOC correlation against discovered assets
- Vulnerability announcement mapping
- Dark web monitoring for exposed data
Automated Alerting
- Critical asset exposure
- Unplanned service deployment
- Security control bypass
- Compliance violations
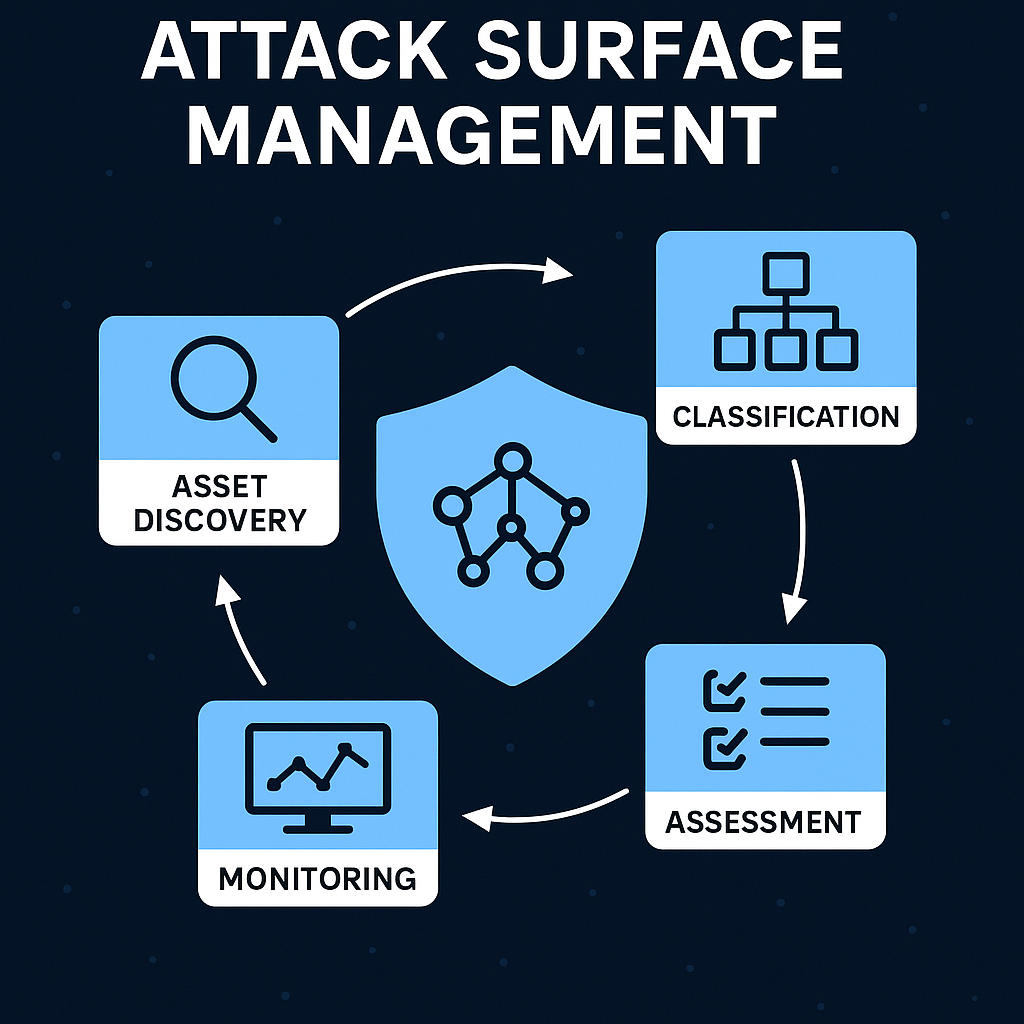
The ASM Methodology
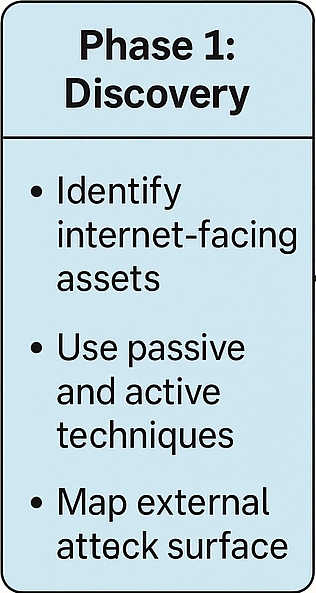
Phase 1: Discovery
Use both passive and active techniques to map your external attack surface.
Passive Techniques:
- DNS enumeration
- Certificate transparency logs
- Search engine reconnaissance
- Social media mining
Active Techniques:
- Port scanning
- Service fingerprinting
- Web application crawling
- API endpoint discovery
Phase 2: Classification
Categorize discovered assets by business function, risk level, and ownership.

Technical Classification:
- Web applications vs. APIs
- Production vs. development
- Internal vs. external intent
- Managed vs. unmanaged
Business Classification:
- Revenue impact
- Data sensitivity
- Regulatory requirements
- Operational criticality
Phase 3: Assessment
Evaluate each asset for security risks and compliance issues.

Security Assessment:
- Exposed services
- Missing security controls
- Known vulnerabilities
- Misconfigurations
Compliance Review:
- Regulatory requirements
- Internal policies
- Industry standards
- Best practices
Phase 4: Monitoring
Implement continuous monitoring for changes and new risks.

Automated Monitoring:
- New asset detection
- Configuration changes
- Security control status
- Threat intelligence correlation
Manual Review:
- High-risk findings
- Policy exceptions
- Business context validation
- Remediation planning
Why ASM is Critical Now
Digital Transformation Impact
Cloud Migration
- Rapid deployment capabilities
- Ephemeral infrastructure
- Multiple cloud providers
- Shadow IT proliferation
DevOps Acceleration
- Continuous deployment
- Microservices architecture
- API-first development
- Development environment exposure
Remote Work Evolution
- Increased endpoint diversity
- New access patterns
- Third-party tool adoption
- Decentralized IT decisions
Threat Landscape Evolution
Automated Reconnaissance Attackers use automated tools to continuously scan for new assets and vulnerabilities. They often discover newly deployed systems before organizations realize they exist.
Supply Chain Focus High-profile attacks like SolarWinds have shown how third-party compromises can provide access to target networks. ASM helps identify these transitive risks.
Zero-Day Exploitation Attackers increasingly target forgotten or unpatched systems where zero-day vulnerabilities provide extended access without detection.
ASM Implementation Challenges
Technical Challenges
Scale Management Large organizations may discover 50,000+ assets, requiring intelligent prioritization and automated processing.
False Positives CDN endpoints, third-party services, and shared infrastructure can generate noise that obscures real risks.
Dynamic Infrastructure Cloud-native applications create ephemeral assets that traditional tools struggle to track.
Organizational Challenges
Cross-Functional Coordination ASM requires cooperation between IT, security, legal, and business units, each with different priorities and processes.
Resource Constraints Comprehensive ASM programs require dedicated tools, skilled personnel, and ongoing operational commitment.
Change Management Organizations must adapt processes, policies, and culture to support continuous asset discovery and monitoring.
Building ASM Business Value
According to the IBM Cost of a Data Breach Report 2025, organizations with comprehensive attack surface visibility reduce breach costs by an average of $4.4 million.
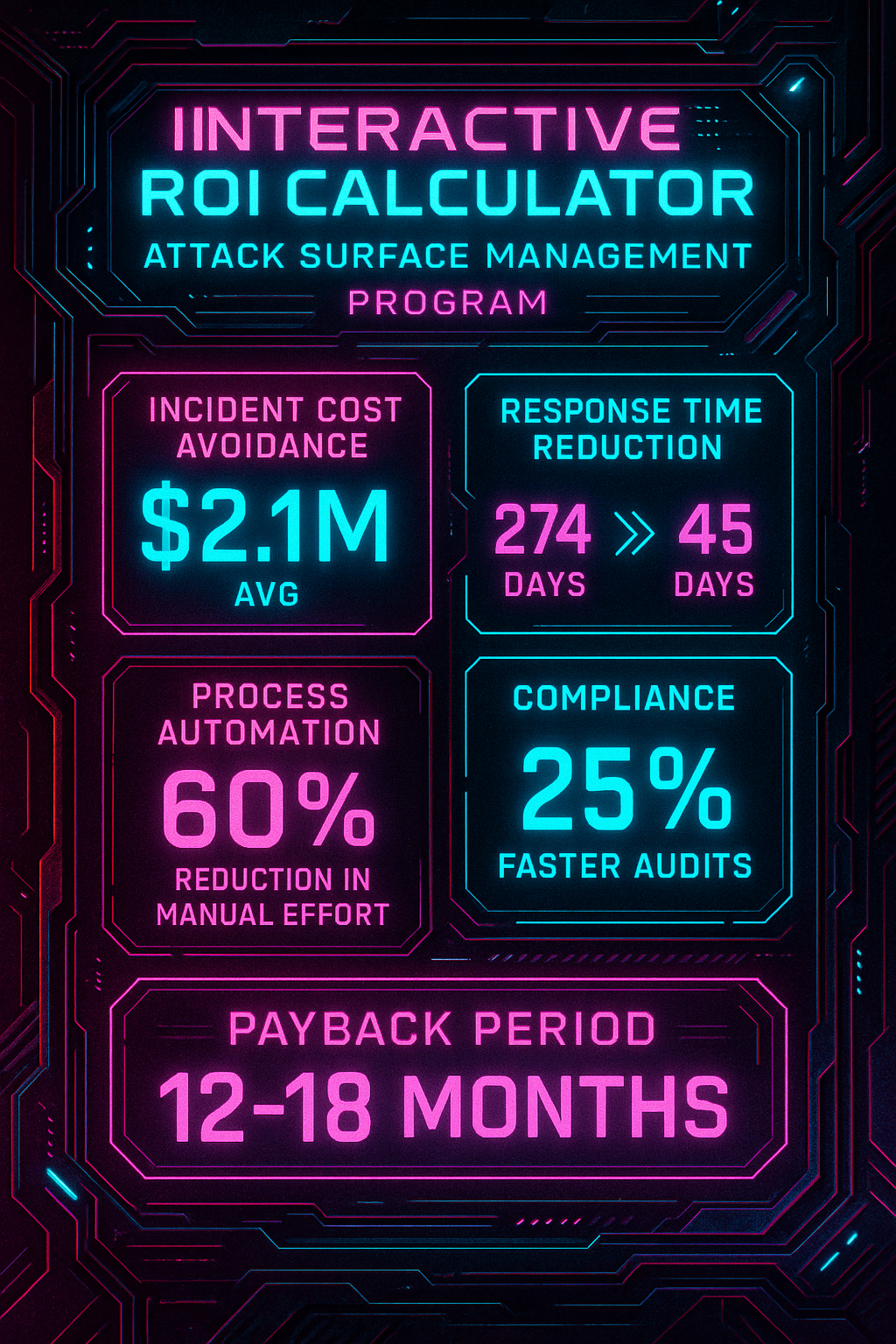
Risk Reduction
- Eliminate unknown attack vectors
- Reduce exposure to external threats
- Prevent data breaches and incidents as documented in Verizon DBIR 2025
- Improve security posture visibility
Compliance Support
- Demonstrate asset inventory completeness per NIST SP 800-53 requirements
- Support regulatory audit requirements
- Track policy compliance across infrastructure
- Maintain security control effectiveness
Operational Efficiency
- Automate asset discovery and classification
- Reduce manual inventory processes
- Prioritize security efforts effectively
- Improve incident response capabilities
ASM Success Factors
Executive Sponsorship
ASM programs require C-level support to overcome organizational silos and secure necessary resources.
Cross-Functional Teams
Successful ASM implementation involves representatives from:
- Security operations
- IT infrastructure
- Cloud architecture
- Legal and compliance
- Business units
Tool Integration
ASM tools must integrate with existing security infrastructure:
- SIEM platforms
- Vulnerability scanners
- Ticketing systems
- Threat intelligence feeds
Continuous Improvement
ASM programs must evolve with changing threat landscapes, business requirements, and technology capabilities.
Getting Started with ASM
Assessment Questions
Before implementing ASM, evaluate your current capabilities:
- Asset Visibility: How many internet-facing assets do you currently know about?
- Discovery Methods: What tools and processes do you use for asset discovery?
- Change Management: How do you track new deployments and modifications?
- Risk Assessment: How do you evaluate security risks for external assets?
- Monitoring Coverage: What percentage of your assets are actively monitored?
Immediate Actions
- Inventory Current Tools: Catalog existing asset discovery and monitoring capabilities
- Identify Gaps: Determine where current processes fall short of ASM requirements
- Pilot Program: Start with a limited scope to demonstrate value and refine processes
- Team Training: Ensure security teams understand ASM principles and methodologies
Success Metrics
- Asset Discovery Rate: New assets identified per month
- Coverage Percentage: Known assets vs. total discovered assets
- Risk Reduction: Measurable decrease in high-risk exposures
- Mean Time to Discovery: How quickly new assets are identified and classified
Next Steps
This article introduced the fundamentals of Attack Surface Management. The next article in this series will dive deep into asset discovery methodologies, covering specific techniques, tools, and processes for comprehensive external reconnaissance.
Coming Next: Attack Surface Management: Asset Discovery Methodologies and Techniques
Key Takeaways
- ASM is Essential: Modern organizations need continuous external asset discovery and monitoring
- External Perspective: See your infrastructure as attackers do, not just as you think it exists
- Continuous Process: ASM requires ongoing commitment, not one-time assessment
- Business Value: Proper ASM reduces risk, supports compliance, and improves operational efficiency
- Holistic Approach: Successful ASM combines people, processes, and technology
Continue with Part 2: Asset Discovery Methodologies to learn specific techniques and tools for comprehensive attack surface discovery.