Attack Surface Management: Asset Classification and Risk Assessment
ASM Asset Classification & Risk Assessment: Expert Guide to Security Prioritization
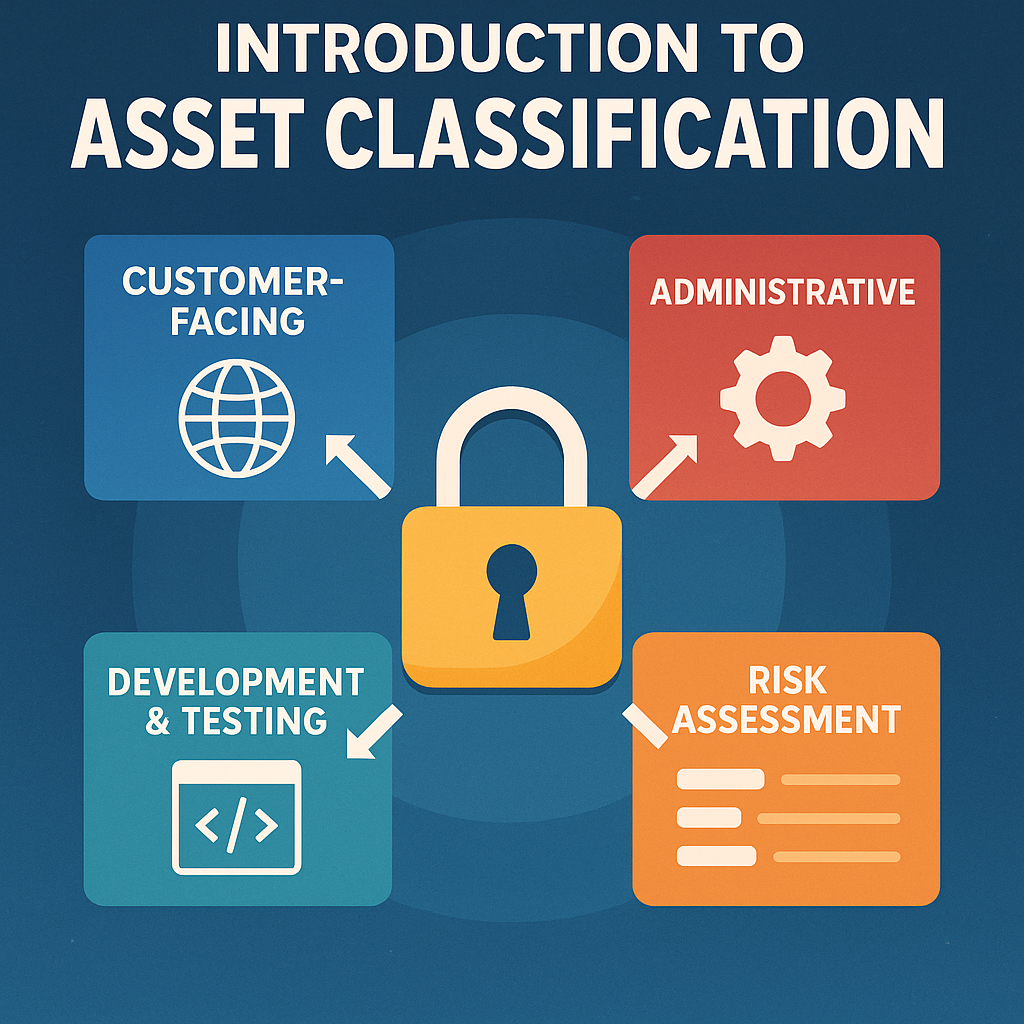
Introduction to Asset Classification
Once you’ve discovered your external attack surface, the next critical step is classification and risk assessment. According to NIST SP 800-30 Rev. 1, effective risk management requires systematic identification, analysis, and evaluation of organizational risks. Raw discovery data without proper classification is overwhelming and often counterproductive. Effective classification enables security teams to focus their limited resources on the assets that matter most to the organization.
Asset classification in ASM differs from traditional IT asset management because it emphasizes external exposure, business impact, and threat likelihood rather than just ownership and configuration. The FAIR (Factor Analysis of Information Risk) framework provides quantitative methods for risk analysis that complement ASM classification efforts. The goal is to understand which assets pose the greatest risk to your organization if compromised.
Series Overview:
- Part 1: ASM Fundamentals - Core concepts and business case for Attack Surface Management
- Part 2: Asset Discovery Methodologies - Comprehensive discovery techniques
- Part 3: Asset Classification & Risk Assessment ← You are here
- Part 4: Continuous Monitoring & Change Detection - Real-time monitoring and alerts
Asset Classification Frameworks
Asset classification represents the critical bridge between raw discovery data and actionable security intelligence. Without proper classification, security teams drown in information while missing critical threats. The key is developing systematic approaches that scale with organizational complexity while maintaining clarity about what matters most.
Functional Classification
Functional classification focuses on what assets do for the business rather than how they’re implemented. This approach aligns security priorities with business objectives and helps communicate risk in terms that stakeholders understand.
Customer-Facing Assets These assets directly serve customers or business partners:
- Public Websites: Marketing sites, product catalogs, corporate information
- Customer Portals: Account management, self-service interfaces
- E-commerce Platforms: Online stores, payment processing
- API Endpoints: Customer-facing APIs, mobile app backends
Risk Consideration: Direct impact on customer experience and business reputation. Often high-value targets for attackers seeking customer data or service disruption.
Customer-facing assets represent the organization’s digital front door. They’re typically well-defended but face constant attack pressure due to their visibility and value. The challenge lies in balancing accessibility with security - these assets must be highly available while protecting sensitive customer data and business operations.
Administrative Assets Internal tools and management interfaces exposed externally:
- Admin Panels: Content management systems, control interfaces
- Remote Access: VPN endpoints, remote desktop gateways
- Monitoring Systems: Dashboards, alert interfaces
- Management APIs: Configuration and control interfaces
Risk Consideration: Highest risk category due to privileged access potential. Compromise often leads to widespread system access.
Administrative assets represent the keys to the kingdom. They’re designed for privileged users and often lack the robust security controls of customer-facing systems. The exposure of administrative interfaces frequently indicates misconfigurations or shadow IT deployments that bypass security review processes.
Development and Testing Assets Non-production environments that may contain sensitive data:
- Development Environments: Active development systems
- Staging Platforms: Pre-production testing
- Quality Assurance: Testing and validation systems
- Sandbox Environments: Experimental and prototype systems
Risk Consideration: Often have weaker security controls but may contain production data copies or provide pathways to production systems.
Development environments present unique challenges for security teams. They’re designed for rapid iteration and often prioritize functionality over security. However, they frequently contain copies of production data, hardcoded credentials, or network pathways that provide access to production systems. The temporary nature of many development deployments means they often escape normal security review processes.
Integration and API Assets Systems facilitating data exchange and business processes:
- Business APIs: Partner integrations, data feeds
- Webhook Endpoints: Event notifications, callbacks
- File Transfer: SFTP, FTP endpoints
- Middleware: Integration platforms, message brokers
Risk Consideration: Can provide access to sensitive business data or serve as pivot points for lateral movement.
Integration assets often operate behind the scenes, making them less visible to security teams while providing critical business functionality. They frequently handle sensitive data flows between systems and partners, making them attractive targets for attackers seeking to access valuable information or establish persistent presence in organizational networks.
Technical Classification
Technical classification provides the foundation for vulnerability assessment and security tool selection. Understanding the underlying technology stack helps predict likely attack vectors and appropriate defensive measures.
By Service Type Understanding the technical nature of each asset:
Web Applications
- Static Sites: HTML/CSS/JavaScript only
- Dynamic Applications: Server-side processing
- Single Page Applications: Client-side frameworks
- Content Management: WordPress, Drupal, custom CMS
Each application type presents different security challenges. Static sites have minimal attack surface but can still be compromised through client-side vulnerabilities or hosting infrastructure issues. Dynamic applications require server-side security controls and present larger attack surfaces. Content management systems often combine both challenges with additional complexity from plugins and customizations.
API Services
- REST APIs: Standard HTTP-based APIs
- GraphQL: Query language APIs
- SOAP: Legacy web services
- gRPC: Modern RPC frameworks
API security has become increasingly critical as organizations adopt microservices architectures. REST APIs dominate modern implementations but often lack proper authentication and authorization controls. GraphQL provides powerful query capabilities but can expose more data than intended. Legacy SOAP services may have outdated security implementations, while gRPC requires specialized security expertise.
Infrastructure Services
- Web Servers: Apache, Nginx, IIS
- Mail Servers: SMTP, IMAP, POP3
- DNS Servers: Authoritative and recursive
- File Servers: FTP, SFTP, WebDAV
Infrastructure services provide fundamental capabilities but often receive less security attention than applications. Web servers require regular updates and proper configuration to prevent common vulnerabilities. Mail servers handle sensitive communications and present attractive targets for attackers. DNS servers can be leveraged for data exfiltration or command-and-control communications.
By Technology Stack
- Programming Languages: PHP, Java, .NET, Python, Node.js
- Frameworks: Spring, Django, Express, Laravel
- Databases: MySQL, PostgreSQL, MongoDB, Redis
- Cloud Platforms: AWS, Azure, GCP services
Technology stack identification drives vulnerability assessment priorities. Each language and framework has characteristic vulnerabilities and security best practices. Understanding the technology stack helps security teams focus their efforts on the most likely attack vectors and select appropriate security tools.
Security Control Classification
Security control classification evaluates the protective measures already in place, providing insight into current risk posture and remediation priorities.
Authentication Requirements
- No Authentication: Publicly accessible
- Basic Authentication: Username/password
- Multi-Factor: Additional verification factors
- Certificate-Based: Client certificate authentication
- SSO Integration: Enterprise identity providers
Authentication requirements directly impact attack difficulty and potential for unauthorized access following NIST SP 800-63B. Public assets require robust application-level controls per OWASP Authentication Cheat Sheet, while authenticated systems need identity and access management integration following NIST SP 800-63C. Multi-factor authentication significantly increases security per CISA MFA Guidance but may impact user experience analyzed in NIST SP 800-63A.
Encryption Status
- HTTP Only: Unencrypted communication
- HTTPS Available: SSL/TLS supported but not enforced
- HTTPS Enforced: Encrypted communication required
- HSTS Enabled: Strict transport security implemented
Encryption status provides immediate insight into data protection capabilities following NIST SP 800-52. HTTP-only communication exposes sensitive data to interception per OWASP Transport Layer Protection, while proper HTTPS implementation protects data in transit according to RFC 8446. HSTS enforcement prevents downgrade attacks per RFC 6797 and ensures consistent encryption analyzed in SSL Labs Best Practices.
Security Headers Evaluate implementation of critical security headers:
# Security header analysis
curl -I https://example.com | grep -E "(X-Frame-Options|X-XSS-Protection|X-Content-Type-Options|Strict-Transport-Security|Content-Security-Policy)"
Security headers provide defense-in-depth against common web application attacks per OWASP Secure Headers Project. Their presence indicates mature security practices following Mozilla Web Security Guidelines, while their absence suggests potential vulnerabilities to clickjacking, XSS, and other client-side attacks documented in OWASP Top 10 A03 and analyzed by Security Headers Scanner.
Risk Assessment Methodology
Risk assessment transforms technical asset information into business-relevant security priorities. The ISO 27005:2022 standard provides comprehensive guidance for information security risk management processes. Effective methodologies balance quantitative analysis with qualitative judgment, providing consistent results while accommodating organizational context.
Impact Assessment
Impact assessment evaluates the potential consequences of asset compromise, considering both direct and indirect effects on business operations, compliance, and reputation. According to NIST SP 800-60, security categorization should consider confidentiality, integrity, and availability impacts.
Data Sensitivity Analysis Classify assets based on the sensitivity of data they process or store:
Public Data (Impact: 1-2)
- Marketing content
- Public documentation
- General corporate information
Public data compromise has minimal direct impact but can affect organizational reputation and provide intelligence for future attacks. The primary concern is ensuring data integrity and availability rather than confidentiality.
Internal Data (Impact: 3-5)
- Employee information
- Business processes
- Operational data
Internal data compromise can disrupt operations and provide attackers with information for social engineering or further attacks. The impact depends on the specific data types and their role in business processes.
Confidential Data (Impact: 6-8)
- Customer personal information
- Financial records
- Proprietary business data
Confidential data compromise can result in significant business impact, including customer loss, competitive disadvantage, and regulatory penalties. This category requires robust protection and careful access control.
Regulated Data (Impact: 9-10)
- Payment card information (PCI DSS)
- Healthcare records (HIPAA) with HITECH Act breach notification requirements
- Personal data (GDPR) and CCPA privacy regulations with significant penalties
Regulated data compromise carries the highest impact due to potential regulatory penalties, legal liability, and reputational damage. These assets require the strongest security controls and continuous monitoring.
Business Process Criticality Evaluate the asset’s role in business operations:
Revenue Generation
- E-commerce platforms: 9-10
- Customer portals: 7-8
- Marketing sites: 3-4
Revenue-generating assets directly impact business operations and financial performance. Their compromise can result in immediate financial losses and long-term customer impact.
Operational Support
- Administrative systems: 8-9
- Monitoring platforms: 6-7
- Documentation sites: 2-3
Operational support assets enable business processes and IT operations. Their compromise can disrupt business operations and provide attackers with administrative access.
Compliance Requirements Assets subject to regulatory oversight require special consideration:
- Financial services: SOX, PCI DSS
- Healthcare: HIPAA, HITECH
- Privacy: GDPR, CCPA
- Government: FedRAMP, FISMA
Compliance requirements add additional impact considerations beyond business operations. Regulatory violations can result in significant penalties and require specific security controls and documentation.
Likelihood Assessment
Likelihood assessment evaluates the probability of successful attack against each asset, considering exposure, vulnerability, and threat actor capabilities.
Exposure Level How easily can attackers discover and access the asset?
Internet Accessible (Likelihood: +3)
- Publicly routable IP addresses
- Indexed by search engines
- Listed in public directories
Internet-accessible assets face constant attack pressure from automated scanners and opportunistic attackers. Their visibility makes them attractive targets for broad-based attacks and vulnerability exploitation.
Discoverable but Hidden (Likelihood: +2)
- Not linked from main sites
- Requires direct URL knowledge
- Found through subdomain enumeration
Hidden assets provide security through obscurity but can be discovered through reconnaissance techniques. They often lack the security controls of public-facing assets while remaining vulnerable to targeted attacks.
Network Accessible Only (Likelihood: +1)
- Requires VPN or internal access
- Network segmentation protected
- Access control restricted
Network-protected assets have reduced exposure but remain vulnerable to insider threats and lateral movement after initial compromise. Their security depends on network controls and access management.
Attack Surface Complexity More complex applications typically have more vulnerabilities:
Simple Static Sites (Likelihood: +1)
- Limited functionality
- Minimal server-side processing
- Few input vectors
Simple static sites have minimal attack surface but can still be compromised through hosting infrastructure vulnerabilities or client-side attacks. Their security depends primarily on proper hosting configuration.
Dynamic Web Applications (Likelihood: +2)
- User input processing
- Database interactions
- Session management
Dynamic applications present larger attack surfaces with multiple potential vulnerability types. Common issues include input validation failures, authentication bypasses, and session management flaws.
Complex API Platforms (Likelihood: +3)
- Multiple endpoints
- Various data formats
- Integration complexity
Complex API platforms have extensive attack surfaces with numerous potential vulnerability classes. They require comprehensive security testing and robust access controls to prevent unauthorized access.
Known Vulnerability Exposure Regular vulnerability assessment reveals:
Current Patches (Likelihood: +0)
- Up-to-date software versions
- Recent security updates applied
- Proactive patch management
Well-maintained systems with current patches have reduced vulnerability exposure. However, zero-day vulnerabilities and configuration issues can still present risks.
Missing Updates (Likelihood: +2)
- Outdated software versions
- Known CVEs unpatched
- Delayed patch deployment
Systems with missing updates have known vulnerabilities that attackers can exploit. The risk depends on vulnerability severity and exploit availability.
End-of-Life Software (Likelihood: +4)
- Unsupported versions
- No security updates available
- Legacy system dependencies
End-of-life software presents the highest vulnerability risk due to lack of security updates. These systems require additional compensating controls or replacement planning.
Risk Scoring Calculation
Risk scoring provides a quantitative framework for comparing and prioritizing assets based on their potential impact and likelihood of compromise.
Quantitative Risk Score Combine impact and likelihood assessments:
Risk Score = (Impact Score × Likelihood Score) / 2
Where:
- Impact Score: 1-10 based on data sensitivity and business criticality
- Likelihood Score: 1-10 based on exposure and vulnerability factors
- Final Risk Score: 1-10 (normalized for practical use)
This formula provides a balanced approach that considers both potential consequences and probability of occurrence. The normalization ensures consistent scoring across different asset types and risk factors.
Risk Level Categories
- Critical (9-10): Immediate attention required
- High (7-8): Priority remediation within 30 days
- Medium (4-6): Standard remediation timeline
- Low (1-3): Monitor and address as resources permit
Risk categories translate numerical scores into actionable priorities for security teams. The timeframes provide clear expectations for remediation efforts based on risk levels.
Example Risk Calculations
E-commerce Platform
- Impact: 9 (revenue generation + customer data)
- Likelihood: 6 (public exposure + complex application)
- Risk Score: (9 × 6) / 2 = 27 → Normalized to 10 (Critical)
This example demonstrates how high-value assets with significant exposure require immediate attention regardless of current security controls.
Development Environment
- Impact: 6 (internal data + potential production access)
- Likelihood: 8 (unintended exposure + weak controls)
- Risk Score: (6 × 8) / 2 = 24 → Normalized to 8 (High)
Development environments often present high risk due to weak security controls and potential access to production systems, despite lower direct business impact.
Marketing Website
- Impact: 3 (public data + brand reputation)
- Likelihood: 4 (public exposure + simple application)
- Risk Score: (3 × 4) / 2 = 6 (Medium)
Marketing websites typically present moderate risk due to limited data sensitivity and simple functionality, despite public exposure.
Advanced Classification Techniques
Manual classification provides deep understanding but doesn’t scale to enterprise requirements. According to research by SANS Institute, organizations with more than 1000 external assets require automated classification to maintain operational efficiency. Advanced techniques combine automated analysis with human expertise to create comprehensive, maintainable classification systems that can adapt to changing infrastructure.
Automated Classification
Automated classification leverages pattern recognition and technical analysis to rapidly categorize large numbers of assets. The key is developing reliable heuristics that can make accurate determinations without human intervention.
Pattern-Based Classification Use URL patterns and response characteristics to automatically classify assets:
# Administrative interface detection
if [[ $url =~ /(admin|administrator|manage|control|dashboard)/ ]]; then
classification="administrative"
risk_modifier="+2"
fi
# API endpoint detection
if [[ $response_content_type =~ application/json ]]; then
classification="api_endpoint"
risk_modifier="+1"
fi
# Development environment detection
if [[ $subdomain =~ ^(dev|test|staging|qa|development) ]]; then
classification="development"
risk_modifier="+3"
fi
Pattern-based classification exploits the predictable naming conventions that most organizations use for their infrastructure. Administrative interfaces often contain obvious keywords that make them easy to identify automatically. This approach works well for initial classification but requires regular updates as organizations evolve their naming conventions.
Technology Fingerprinting Identify technologies to assess vulnerability exposure:
# Web technology detection
curl -I https://example.com 2>/dev/null | grep -i server
curl -I https://example.com 2>/dev/null | grep -i x-powered-by
# Framework detection from response patterns
curl -s https://example.com | grep -i -o "powered by [^<]*"
curl -s https://example.com | grep -i -o "built with [^<]*"
Technology fingerprinting provides crucial intelligence for vulnerability assessment and security tool selection. Different technologies have characteristic vulnerabilities and require specific security approaches. Automated fingerprinting ensures that security teams understand the technology landscape without manual investigation of every asset.
Certificate Analysis for Classification SSL certificates provide classification clues:
# Certificate subject analysis
echo | openssl s_client -connect example.com:443 2>/dev/null | \
openssl x509 -noout -subject | \
grep -o "CN=[^,]*"
# Certificate issuer analysis
echo | openssl s_client -connect example.com:443 2>/dev/null | \
openssl x509 -noout -issuer
Certificate analysis reveals organizational structure and security practices. Certificate subjects often contain environment information (dev, staging, prod) that helps with classification. Certificate issuers indicate security practices - internal CAs might suggest development environments while commercial CAs indicate production systems.
Business Context Integration
Technical classification provides the foundation, but business context determines priority and resource allocation. Effective classification systems integrate technical analysis with business understanding to create actionable security priorities.
Asset Ownership Mapping Connect technical assets to business ownership:
Organizational Mapping
- Business unit responsible
- Technical team ownership
- Vendor/contractor managed
- Shadow IT deployment
Understanding asset ownership is crucial for effective security management. Business units must take responsibility for their assets’ security, while technical teams need clear accountability for implementation. Shadow IT deployments often lack proper security controls and require special attention.
Budget and Compliance Tracking
- Budget allocation responsibility
- Compliance scope inclusion
- Audit requirements
- Change management process
Financial and compliance context helps prioritize security investments. Assets with dedicated budgets can receive appropriate security controls, while compliance-scoped assets require specific attention. Understanding change management processes helps ensure that security controls remain effective as assets evolve.
Service Level Requirements
- Uptime expectations
- Performance requirements
- Security control standards
- Monitoring expectations
Service level requirements provide context for security control selection. High-availability assets require security controls that don’t impact operations, while performance-sensitive assets need efficient security implementations. Understanding these requirements helps balance security with operational needs.
Risk Prioritization Strategies
Risk prioritization transforms assessment results into actionable security programs. The NIST Cybersecurity Framework emphasizes risk-informed decision-making that aligns cybersecurity activities with business requirements and risk tolerance. Effective strategies balance quantitative risk scores with qualitative factors like threat intelligence, business priorities, and resource constraints.
Risk-Based Prioritization
Risk-based prioritization focuses resources on assets that pose the greatest combined threat to organizational objectives. This approach, supported by frameworks like FAIR (Factor Analysis of Information Risk), maximizes security impact while working within resource constraints.
Critical Asset First Focus immediate attention on assets with highest combined risk scores:
- Customer-facing applications with sensitive data
- Administrative interfaces with high privileges
- Unintended exposures of internal systems
- Vulnerable systems in high-exposure locations
This approach ensures that the most dangerous combinations of impact and likelihood receive immediate attention. Customer-facing applications with sensitive data represent the highest business risk, while administrative interfaces provide the greatest potential for widespread compromise.
Business Impact Prioritization When resources are limited, prioritize by business impact:
- Revenue-generating systems
- Compliance-critical assets
- Operational support systems
- Brand and reputation assets
Business impact prioritization aligns security efforts with organizational priorities. Revenue-generating systems require immediate attention because their compromise directly affects business operations. Compliance-critical assets need attention to avoid regulatory penalties.
Threat-Based Prioritization Align with current threat intelligence:
- Assets matching known threat actor targets
- Technologies with active exploit campaigns
- Services exposed to geographic threat regions
- Assets with known compromise indicators
Threat-based prioritization focuses on assets that attackers are actively targeting. This approach requires integration with threat intelligence feeds and understanding of current attack campaigns. Geographic threat considerations are particularly important for organizations with global operations.
Resource Allocation Models
Resource allocation models help organizations manage security efforts within practical constraints. Effective models balance comprehensive coverage with focused attention on high-risk assets.
Security Team Capacity Allocate remediation efforts based on team capabilities:
Immediate Response (24-48 hours)
- Critical vulnerabilities on high-value assets
- Unintended exposure of sensitive systems
- Active compromise indicators
- Regulatory compliance violations
Immediate response efforts require dedicated resources and established procedures. These situations demand rapid action to prevent or contain security incidents. Clear escalation procedures ensure that critical issues receive appropriate attention.
Short-term Projects (1-4 weeks)
- High-risk vulnerability remediation
- Security control implementation
- Asset configuration hardening
- Access control improvements
Short-term projects provide structured approaches to addressing significant security gaps. These efforts require project management and coordination across multiple teams. Success depends on clear objectives and dedicated resources.
Long-term Initiatives (1-6 months)
- Architecture improvements
- Technology upgrades
- Policy and process changes
- Comprehensive security assessments
Long-term initiatives address fundamental security issues that require sustained effort. These projects often involve significant organizational change and require executive support. Success depends on maintaining momentum and measuring progress.
Classification Documentation and Tracking
Effective classification systems require comprehensive documentation and tracking capabilities. Without proper records, classification efforts become inconsistent and lose value over time.
Asset Registry Maintenance
Asset registries provide the foundation for effective classification and risk management. They must balance comprehensive information with practical usability.
Essential Asset Attributes Maintain comprehensive records for each classified asset:
asset_id: "AST-2024-001"
url: "https://api.example.com"
ip_address: "203.0.113.10"
discovery_date: "2024-01-15"
classification:
functional: "api_endpoint"
technical: "rest_api"
security: "authenticated"
risk_assessment:
impact_score: 7
likelihood_score: 6
risk_score: 7
risk_level: "high"
business_context:
owner: "Product Team"
criticality: "revenue_supporting"
compliance_scope: ["PCI_DSS", "GDPR"]
technical_details:
technologies: ["nginx", "nodejs", "mongodb"]
authentication: "api_key"
encryption: "tls_1.3"
security_controls:
waf_protected: true
rate_limiting: true
monitoring: true
last_assessed: "2024-01-15"
next_review: "2024-04-15"
This structured approach ensures that all relevant information is captured and maintained. The YAML format provides human-readable documentation while supporting automated processing. Regular updates ensure that classifications remain current as assets evolve.
Change Tracking Monitor asset classification changes over time:
- Risk score trends
- Classification updates
- New security controls
- Remediation progress
Change tracking provides insight into security program effectiveness and helps identify trends that require attention. Risk score trends indicate whether security efforts are improving organizational posture. Classification updates reflect changes in business priorities or threat landscape.
Reporting and Visualization
Effective reporting translates classification data into actionable insights for different stakeholders. Reports must be tailored to audience needs while maintaining accuracy and completeness.
Executive Dashboards Present classification data for business leaders:
- Risk distribution by business unit
- High-risk asset counts and trends
- Remediation progress metrics
- Compliance coverage status
Executive dashboards focus on business-relevant metrics that support decision-making. Risk distribution by business unit helps identify areas that need additional resources. Remediation progress metrics demonstrate security program effectiveness.
Technical Team Reports Provide actionable information for security teams:
- Assets requiring immediate attention
- Vulnerability correlation analysis
- Technology stack risk analysis
- Remediation priority queues
Technical reports provide the detailed information that security teams need for daily operations. Priority queues help manage workload and ensure that high-risk assets receive appropriate attention. Vulnerability correlation analysis helps identify systemic issues.
Compliance Reporting Generate compliance-specific views:
- Assets in regulatory scope
- Control implementation status
- Audit trail documentation
- Exception and risk acceptance tracking
Compliance reporting addresses regulatory requirements and audit needs. These reports must provide comprehensive documentation of security controls and their effectiveness. Exception tracking ensures that accepted risks are properly documented and reviewed.
Integration with Security Operations
Classification and risk assessment become most valuable when integrated with operational security processes. Integration ensures that assessment results drive security actions rather than remaining as documentation.
SIEM Integration
Security Information and Event Management (SIEM) systems benefit significantly from asset classification data. This integration provides context for alert prioritization and incident response.
Asset Context Enrichment Feed classification data into security monitoring:
{
"asset_id": "AST-2024-001",
"url": "https://api.example.com",
"risk_level": "high",
"business_criticality": "revenue_supporting",
"compliance_scope": ["PCI_DSS"],
"security_controls": {
"waf_protected": true,
"authentication_required": true
}
}
Context enrichment transforms generic security alerts into prioritized incidents. High-risk assets receive immediate attention, while compliance-scoped assets trigger specific response procedures. This integration ensures that security operations focus on the most important threats.
Alert Prioritization Use asset classification to prioritize security alerts:
- Critical alerts from high-risk assets
- Elevated response for compliance assets
- Context-aware incident response
- Risk-based escalation procedures
Alert prioritization prevents important security events from being lost in noise. High-risk assets generate high-priority alerts that receive immediate attention. Compliance assets trigger specific response procedures to address regulatory requirements.
Vulnerability Management Integration
Vulnerability management programs benefit from asset classification through improved prioritization and resource allocation.
Risk-Based Scanning Prioritize vulnerability assessments based on asset classification:
- More frequent scanning of high-risk assets
- Comprehensive testing for critical systems
- Focused assessments for compliance assets
- Continuous monitoring for administrative interfaces
Risk-based scanning ensures that security testing efforts focus on the most important assets. High-risk assets receive more frequent and comprehensive testing, while lower-risk assets receive standard assessment schedules.
Remediation Prioritization Combine vulnerability severity with asset risk:
- Critical vulnerabilities on high-risk assets: Immediate
- High vulnerabilities on medium-risk assets: 30 days
- Medium vulnerabilities on low-risk assets: 90 days
- Low vulnerabilities: Next maintenance cycle
Remediation prioritization ensures that security efforts focus on the most significant risks. This approach balances vulnerability severity with asset importance to maximize security impact.
Common Classification Challenges
Classification efforts face both technical and organizational challenges that can limit effectiveness. Understanding these challenges helps organizations develop more robust classification systems.
Technical Challenges
Technical challenges arise from the complexity and dynamic nature of modern infrastructure. Organizations must address these challenges to maintain effective classification.
Dynamic Infrastructure
- Ephemeral cloud resources
- Auto-scaling applications
- Container-based deployments
- Serverless functions
Dynamic infrastructure challenges traditional classification approaches that assume stable assets. Ephemeral resources may exist for hours or days, making manual classification impractical. Auto-scaling applications change their attack surface based on demand. Container-based deployments create numerous short-lived assets that require automated classification.
Incomplete Information
- Limited asset documentation
- Unknown technology stacks
- Unclear business ownership
- Missing compliance requirements
Incomplete information limits classification accuracy and effectiveness. Many organizations lack comprehensive asset documentation, making it difficult to understand business context. Unknown technology stacks prevent accurate vulnerability assessment. Unclear ownership makes it difficult to assign remediation responsibility.
Organizational Challenges
Organizational challenges often prove more difficult to address than technical issues. Success requires stakeholder alignment and process integration.
Stakeholder Alignment
- Different risk perspectives
- Competing business priorities
- Resource allocation conflicts
- Change resistance
Stakeholder alignment requires balancing different perspectives on risk and priority. Business units may prioritize functionality over security, while security teams focus on risk reduction. Resource allocation conflicts arise when remediation efforts compete with business initiatives.
Process Integration
- Existing asset management processes
- IT service management alignment
- Security policy compliance
- Change control procedures
Process integration ensures that classification efforts support rather than conflict with existing organizational processes. Asset management processes may use different classification schemes that require reconciliation. IT service management alignment ensures that classification supports operational needs.
Next Steps
Asset classification and risk assessment provide the foundation for prioritized security efforts. The next article in this series will cover continuous monitoring and change detection, showing how to maintain accurate asset visibility and respond to changes in your attack surface.
Coming Next: Attack Surface Management: Continuous Monitoring and Change Detection
Key Takeaways
- Structured Classification: Use consistent frameworks for functional, technical, and security classification
- Risk-Based Prioritization: Combine impact and likelihood assessments for effective resource allocation
- Business Context: Integrate business requirements and compliance needs into classification
- Automation Essential: Implement automated classification to handle scale effectively
- Continuous Updates: Regularly review and update classifications as assets and threats evolve
Continue with Part 4: Continuous Monitoring and Change Detection to learn how to maintain visibility and respond to attack surface changes.